Linux Generate Ssl Key With Subjectaltname
Posted : admin On 15.04.2020The software described in this documentation is either no longer supported or is in extended support.
Oracle recommends that you upgrade to a current supported release.
The openssl command doesn’t provide a way to include extensions like the subjectAltName without writing a config file first. I have written a simple utility that does it all automatically. $ openssl genrsa -out private.key 3072 $ openssl req -new -x509 -key private.key -sha256 -out certificate.pem -days 730 You are about to be asked to enter information that will be incorporated into your certificate request.
- Apr 09, 2020 Generate a server private key using a utility (OpenSSL, cfssl etc) Create a CSR using the server private key. Generate the server certificate using CA key, CA cert and Server CSR. Also Read: Types of SSL/TLS Certificates Explained. This guide explains the steps required to create CA, SSL/TLS certificates using the following utilities.
- Dec 31, 2018 Generate/sign CSR with subject Alternative Name (SAN) - CentOS7/RHEL7. This article will guide you through generating and signing a CSR and at the same time including SubjectAltName within the request.
- Create the certificate key openssl genrsa -out mydomain.com.key 2048 Create the signing (csr) The certificate signing request is where you specify the details for the certificate you want to generate. This request will be processed by the owner of the Root key (you in this case since you create it earlier) to generate the certificate.
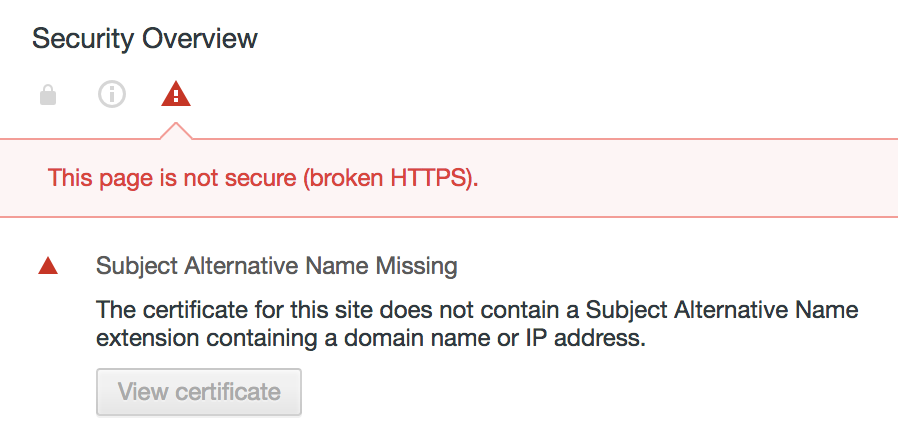
1.8.5 SSL SecurityWarning: Certificate has no subjectAltName
When you configure a Ceph Object Gateway instance and enable SSL you must create an SSL certificate. If the certificate does not have the v3 extension enabled and the subjectAltName set within the certificate, a warning message is displayed when a client such as the Swift client attempts to access the gateway:
If a subjectAltName extension of type dNSName is present, this is used as the identity. Otherwise, the Common Name field in the Subject field of the certificate is used. Although the use of the Common Name is existing practice, it is deprecated and Certification Authorities are encouraged to use the dNSName instead.
To prevent the warning from appearing at all, do the following:
Counter strike condition zero key generator. Nothing can stop us, we keep fighting for freedomdespite all the difficulties we face each day.Last but not less important is your own contribution to our cause. This should be your intention too, as a user, to fully evaluate Counter-Strike Condition Zero Keygen withoutrestrictions and then decide.If you are keeping the software and want to use it longer than its trial time, we strongly encourage you purchasing the license keyfrom Counter-Strike official website. This release was created for you, eager to use Counter-Strike Condition Zero Keygen full and with without limitations.Our intentions are not to harm Counter-Strike software company but to give the possibility to those who can not pay for any pieceof software out there. Our releases are to prove that we can!
In the working directory where you are generating the key and certificate, create a copy of the template OpenSSL configuration file:
Modify the configuration file template at
./openssl.cnfand make the following changes:In the section
[ req ]make sure that the following line is uncommented and not preceded with a # character:In the section
[ v3_req ], add the following line to the end of the parameters in this section:Add a section to the end of the configuration file:
Replace
hostname.example.comwith the fully qualified domain name for the host that you are creating the certificate for.
Generate your certificate key, as normal:
Kaspersky internet security activation code free. Use the certificate key and the new
openssl.cnffile to create a Certificate Signing Request (CSR):You may either use the generated CSR to obtain a signed certificate from a recognized Certificate Authority (CA). Or, for testing purposes, you may use this to generate a self-signed certificate as follows:
Create a new configuration file,
v3.cnf, that can host the information for the v3 requirements. Edit it to contain the following lines:Run the following OpenSSL command to generate a self-signed certificate using the CSR and your local key:
Copy the key, CSR and certificate to the usable location on the host:
Create a single PEM file containing both the key and certificate, that can be used by the Ceph Object Gateway when it is started:
(Bug 24424028)
Linux Generate Ssl Key With Subjectaltname Windows 7
Copyright © 2019, Oracle and/or its affiliates. All rights reserved. Legal Notices